Ever wondered how wireless, video, and data services are managed on your computer? Network engineers design and maintain the computer networks that handle all that. Since computer networks aren’t going anywhere, a network engineer has favorable job prospects. Today’s network engineer brings in an average $90,000+ per year in the US.
Are you considering network engineering as a career? Or perhaps you’ve already started to seek a more senior role. We’ve put together this comprehensive list of network engineer interview questions to help you out!
We’ll cover the most basic questions, along with trickier networking troubleshooting interview questions. Let’s get started!
Expect a mix of both behavioral and technical networking interview questions. You might be asked about common web tools like VPN servers or web tools you’ve worked with to build computer networks. Similarly, you might have to recount past work experiences where you demonstrated strong communication or liaising experience.
We’ve separated our list of computer networks interview questions by difficulty to help you find the ones most relevant to your experience.
Let’s start with basic networking questions.
Looking for an entry-level role? Start with these network support engineer interview questions.
Take your time reviewing these interview questions on networking for freshers. You might consider having a few research tabs open to ease your studies, too.
"Cat 5" and "Cat 6" are the LAN cable types most often used. The speed limits for "Cat 5" and "Cat 6" are 100 Mbps and 1 Gbps, respectively.
A cross table connects same-type devices for interaction without needing a switch or hub.
Cross cable and standard LAN cables differ in the manner that the paired wires are joined to the connector (RJ45).
The theoretical length is 100 meters, however, after you pass 80 meters, the signal loss may cause your speed to decline.
The Active Directory is a directory service that manages network environments’ identities and connections. It is a collection of processes and services that help users leverage network resources to accomplish their tasks.

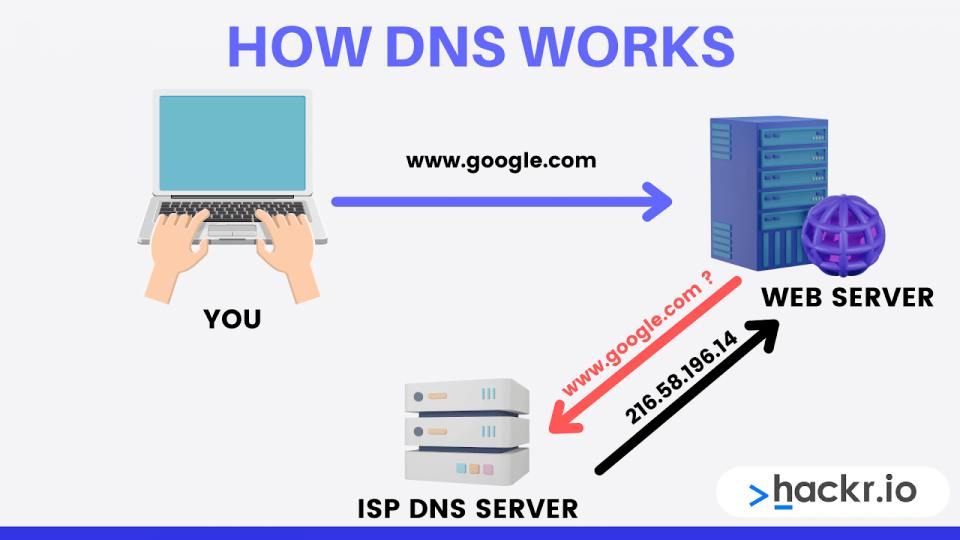
Domain Naming Service, or DNS, is used to translate between names and IP addresses. While we can easily recall names, the computer can only understand numbers. Therefore, we give computers and websites names. When we use these names (such as yahoo.com), the computer converts the request to an IP address (a number) via DNS.
The IPCONFIG command displays IP information assigned to a computer. We can determine the computer's assigned IP address, DNS IP address, and gateway IP address from the output.
The Windows client machine automatically assigns itself an IP address known as an APIPA when a DHCP server is unavailable, to communicate with other network computers.
When we install Active Directory, a domain is formed. It's a security barrier that controls computers inside of it. Using a domain, you can centrally manage computers and control them with group policies.
BSOD stands for “Blue Screen of Death.” A blue screen with a code appears when a hardware or OS issue prevents the Windows operating system from functioning. The best solution is to boot from the "Last Known Good Configuration" on the PC. Boot the machine in safe mode. And if that doesn’t work, it could signify issues with the devices or driver.
RIS stands for Remote Installation Services. Once the installed image has been saved to a Windows server, RIS can set up the new hardware. It can be used to deploy server and client operating systems.
Ghosting, also known as imaging, accomplishes the same task by capturing an installed image and later installing it on new hardware. Because installing an OS from a CD every time might be time-consuming, we choose either RISE or imaging/ghosting.
You can set up a different system and install the most recent versions of the OS and antivirus software. Then, connect the infected HDD to the system as a secondary disc. After that, wipe and scan the backup HDD. Now, you can transfer the files to the new system.
Manageable switches are customizable, configurable, and controllable. Unmanageable switches don’t have any customizable or configurable settings.
NIC stands for network interface controller — a piece of computer hardware also known as a network card or network adapter. An NIC enables computer communication over a computer network.
USB stands for Universal serial bus, which connects devices like modems, mouses, and keyboards.
The connectivity between two devices is something we refer to as a link. It comprises cables and protocols used so two devices can talk to one another.
RAS, or remote access services, connects remote access to resources that might normally reside on a network of IT devices.
Extended ACLs are source- and destination-based. Standard ACLs are source-based.
FTP stands for File Transfer Protocol, which is a communication protocol for exchanging files between computer systems over a network. A user can access files on public servers using anonymous FTP.
A backbone network is a centralized infrastructure created to provide several networks with varied routes and data. It also manages channel and bandwidth control.
Forward lookup converts names to IP addresses, while reverse lookup translates IP addresses to names.
Applying for an associate-level role? Prepare with networking interview questions for experienced network engineers.
Routing chooses the traffic path across multiple networks, between two networks or within a network. Different types of networks, such as computer networks and circuit-switching networks, support routing. Routing entails making decisions to direct data packets from the source to the destination.
Your device will be configured as a router if it has at least two additional interfaces in addition to lo0, or if it has at least one point-to-point interface.
Solaris 2.x: When the computer has two or more interfaces, the IP layer typically behaves as a router (forwarding datagrams that are not addressed to it, among other things). By setting the /dev/ip variable ip forwarding with ndd(1M), you can override this behavior. 0 indicates do not proceed, and the number 1 indicates proceed.
A fully qualified domain name (FQDN) ends with a null or empty string (FQDN).
A partially qualified domain name does not end with a null string (PQDN). A PQDN does not finish at the root; rather, it begins at a node.
Each device (such as a computer or printer) in a computer network that uses Internet Protocol (IP) is assigned a numerical label known as an Internet Protocol address (IP address). The IP of your system or device uniquely identifies it from a large network of computers.
A hub and a switch are both networking devices that help you connect to various devices. The hub is the layer 1 device, i.e., it works at the physical layer and sends the signal to the port. Meanwhile, the switch is a layer 2 device that routes and transmits information over a network.
The following table highlights the key differences between a hub and a switch:
Hub
Switch
Works at layer 1, i.e., the physical layer.
Works at layer 2, i.e., the data link layer.
Follows a broadcast transmission.
Follows the broadcast, unicast, and multicast transmission.
Leverages half duplex transmission technique.
Leverages full-duplex communication technique.
Has 24 to 28 ports.
A layer divides the PDU (protocol data unit) process entirely logically. They specify the method by which data is sent through a network from one machine to another.
TCP is the Transmission Control Protocol and IP is the Internet Protocol.
A host or router can utilize the address resolution protocol (ARP), which determines the physical address of another host on its network by sending an ARP query packet with the recipient's IP address. When a host just knows its physical address, the reverse address resolution protocol (RARP) enables it to find its Internet address.
Clients and servers collaborate as different logical entities to complete a network task.
It is the LAN card's 48-bit hardware address. The network adapter card typically keeps the MAC address in ROM, and it is distinct.
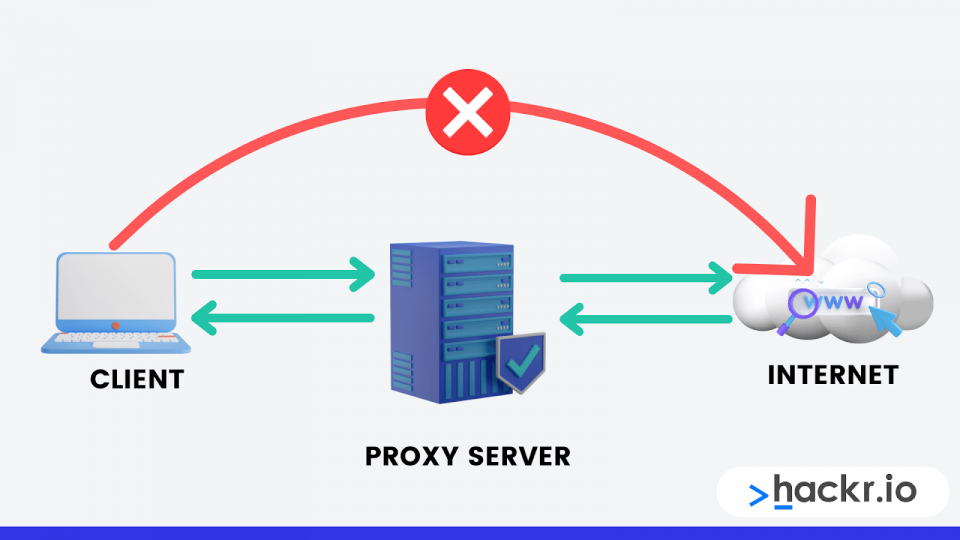
A proxy server conducts the heavy lifting of accessing and retrieving for users similar to how a DNS server caches the addresses of accessed websites. Additionally, proxy servers maintain a list of websites, whether they are whitelisted or banned, to protect consumers from easily avoidable viruses.
These days, most big enterprises and institutions use proxies to enhance network performance.
The big brother of HTTP, HTTPS stands for Secure HTTP (not to be confused with HTTPS, a separate protocol). HTTPS, which was created for identity verification, uses SSL certificates to confirm the server you are connected to is authentic. Although HTTPS has certain encryption capabilities, they are typically judged insufficient, and additional encryption methods are preferred whenever practical. TCP port 443 is used for HTTPS transmission.
Gunning for a senior position or leadership role in network engineering? Don’t attend the interview until you review these interview questions for network engineers in executive roles.
One of the big legacy protocols that ought to be phased out is FTP or File Transfer Protocol. FTP may resume downloads if they are paused and are primarily intended for massive file transfers. There are two methods for gaining access to an FTP server: Anonymous access and Standard Login.
The main difference between the two is that while a Standard Login requires an active user login, Anonymous access does not. The user's credentials are delivered in cleartext using FTP, which makes it exceedingly easy for anyone listening on the wire to sniff the credentials. This is where the main issue with FTP resides.
SSH, or Secure Shell, is most popular among Linux users but has a wide range of applications. Systems, switches, thermostats, or toasters, may all be connected securely over a tunnel, thanks to SSH. SSH also offers the unique ability to act as a tunnel for other programs, which is conceptually comparable to a VPN. If configured properly, even insecure programs or programs operating via insecure connections can be used in a secure state.
ICMP stands for Internet Control Message Protocol. Its main function is to inform systems when they attempt a remote connection whether the other end is accessible.
IPX, or Internetwork Packet Exchange, was a fairly lightweight protocol, which was advantageous given the limitations of computers at the time. It is a TCP/IP rival that performs admirably in small networks, has little to no configuration, and does not require components like DHCP. However, it does not scale effectively for applications like the Internet. As a result, it was abandoned and is no longer a necessary protocol for the majority of pieces.
Almost every Apple software comes with a tool called Bonjour that controls several of the company's automated discovery techniques. Bonjour is a cross between IPX and DNS.
With little to no configuration needed, Bonjour uses mDNS (multicast DNS) to find broadcasting devices on the network. Due to potential security risks, many administrators will purposefully stop this service in a corporate setting. However, in a home setting, it can be up to the user to decide whether the risk is worth the convenience.
A firewall is a network security device that supervises traffic entering and leaving a network. Its primary purpose is to create a barrier between the internal network and external sources to avoid malicious traffic, like viruses or malware.
The network can learn its size from its subnet mask. An address will be treated internally as a component of the local network when it is inside the mask. Since it is not a member of the local network while it is outside, it will be handled differently.
A local host can download files from a distant host using the trivial file transfer protocol (TFTP), but it lacks security and reliability. It uses UDP's basic packet delivery functions.
The usual method offered by TCP/IP for copying a file from one host to another is the File Transfer Protocol (FTP). It is dependable and secure because it uses TCP's services. It creates two links (virtual circuits) between the hosts, one for informational control and the other for data transport.
There are four kinds of networking devices:
Repeater
Repeater, also known as a regenerator, is a technological gadget that only works at the physical layer. Before the network signal deteriorates, it captures it, regenerates the original bit pattern, and then reinserts the updated copy into the link.
Bridges
In identical-type LANs, bridges function at both the physical and data link layers. They separate a bigger network into more manageable sections.
Routers
They pass packets between several interconnected networks (i.e., LANs of different types). They function in the network, data link, and physical layers. Their software enables them to choose the optimal transmission path among the several options.
Gateways
They act as a packet relay between networks using various protocols (e.g., between a LAN and a WAN). Before forwarding it, they receive a packet formatted for one protocol and change it to be formatted for a different protocol. They function across all seven OSI model layers.
There are three important topologies for networks:
BUS topology: Each computer in a BUS architecture connects to a single line of principal network cables. It’s affordable and simple to set up, comprehend, and extend.
STAR topology: A single hub connects every system, making it easy to troubleshoot and reinstall.
RING topology: A single computer connects to two other computers from the rear and front ends. When all computers connect, they form a ring-like structure. This ensures equal access to network resources for all computers and less signal degradation compared to other topologies.
Two transmission media are available: guided and unguided.
Guided Media, such as twisted-pair, coaxial cable, and fiber-optic cable, act as a conduit from one device to another. Any of these media's physical boundaries direct and confine a signal as it travels along them. Metallic materials that accept and transport signals in the form of electrical current are used in twisted-pair and coaxial cables. A glass or plastic cable called an optical fiber accepts and transmits signals in the form of light.
Unguided Media is wireless media that transmits electromagnetic waves without a physical conductor. Signals can be sent through the air. Radio communication, satellite communication, and mobile telephony are used for this.
Transmission entails the physical movement of information, which raises concerns about things like bit polarity, synchronization, clocks, etc. Communication is the complete information exchange between two communication media.
The three types of routing tables are fixed, dynamic, and fixed central.
A hybrid, or both the Distance Vector and Link State Routing protocol methods, offer these benefits:
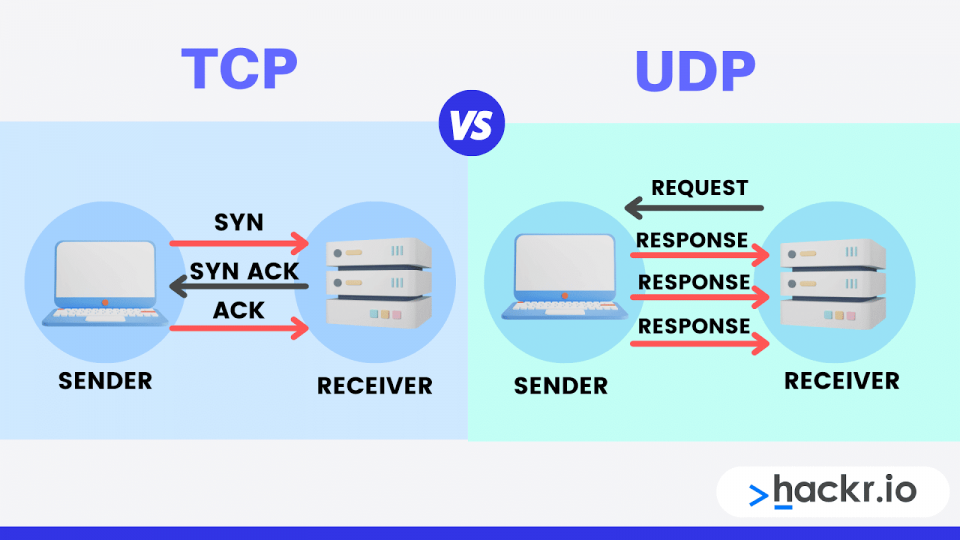
UDP stands for User Datagram Protocol. It is a communication protocol for computer applications to transmit messages, here known as datagrams, to other hosts on a network that follows the Internet Protocol (IP). It is a connectionless communication protocol.
Congrats! You’ve made it to the end of our networking interview questions and answers.
Here are some additional tips to keep in mind along the way:
Don’t be anxious about your next network engineer interview. You have tons of resources, like these network engineer questions, to help you prepare.
Remember to download the Network Engineer Interview Questions and Answers PDF to prepare offline from anywhere and on any device.
But don’t stop there. Consider reading ethical hacking books to whet your appetite, or go further with courses and tutorials.
Start by reviewing our extensive list of computer network interview questions. You might grab a friend to practice in a mock interview. Then, consider finding online tutorials and courses to help apply your knowledge in preparation for technical questions.
Employers observe candidates and their demonstration of certain skills during network engineer interviews.
Here are some essential skills and knowledge for a network engineer:
If you thrive in the IT world, network engineer roles should suit you well. However, you might have to juggle many technical tasks concurrently, which could feel stressful.